The Aes Cipher Consists of N Rounds, Where the Number of Rounds Depends on the
The input to the encryption and decoding algorithms is a single 128-bit block. In FIPS PUB 197, this block is depicted as a 4 * 4 square matrix of bytes.
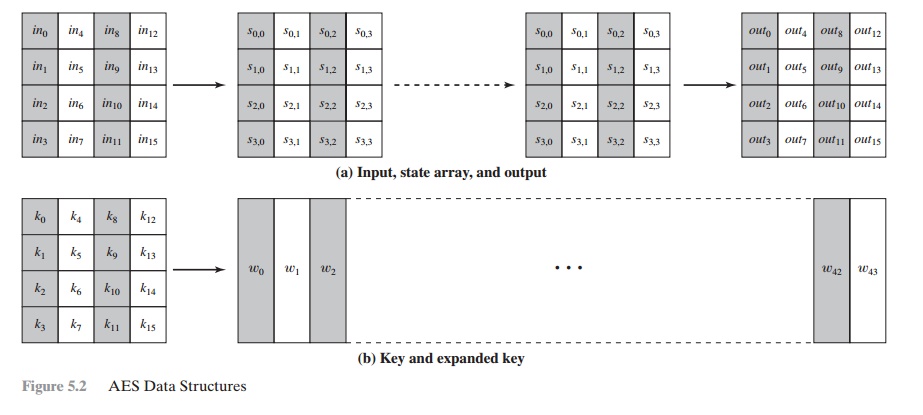
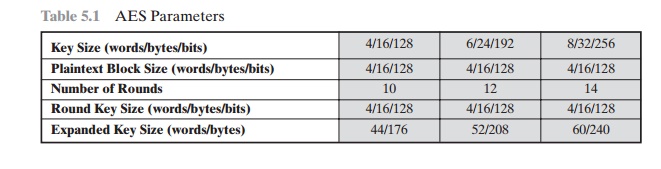
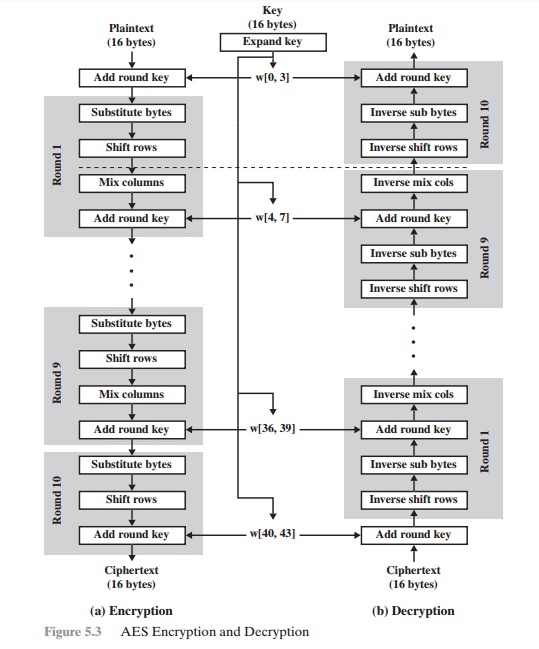
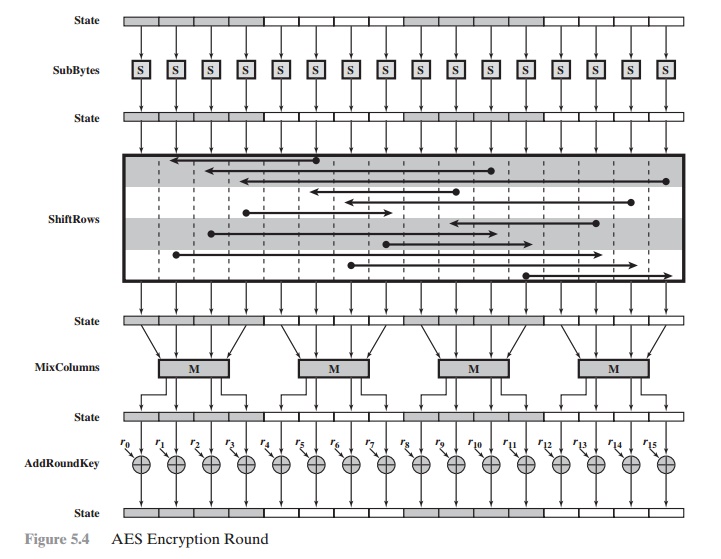
AES STRUCTURE Oecumenical Structure Figure 5.1 shows the whole structure of the AES encryption cognitive process. The cipher takes a plaintext block up size of 128 bits, or 16 bytes. The nam length can Be 16, 24, surgery 32 bytes (128, 192, operating room 256 bits). The algorithm is referred to as AES-128, AES-192, OR AES-256, depending on the key length. The stimulant to the encryption and decryption algorithms is a single 128-snatch block. In FIPS PUB 197, this block is pictured as a 4 * 4 second power matrix of bytes. This block is copied into the State array, which is modified at for each one leg of encryption or decryp- tion. After the concluding stagecoach, DoS is copied to an output matrix. These trading operations are depicted in Figure 5.2a. Likewise, the key is depicted as a square ground substance of bytes. This key fruit is then swollen into an array of key schedule speech. Figure 5.2b shows the enlargement for the 128-chip key. Each Book is four bytes, and the total key schedule is 44 words for the 128-fleck nam. Note that the ordination of bytes inside a matrix is away col- umn. So, for example, the first four bytes of a 128-bit plaintext input to the encryption cipher worry the prototypical column of the in matrix, the second tetrad bytes occupy the second column, and and so along. Similarly, the first 4 bytes of the dilated key, which fles a word, worry the prototypal column of the w intercellular substance. The cipher consists of N rounds, where the come of rounds depends on the key length: 10 rounds for a 16-byte paint, 12 rounds for a 24-byte key, and 14 rounds for a 32-byte key (Table 5.1). The first N - 1 rounds consist of four distinct trans- formation functions: SubBytes, ShiftRows, MixColumns, and AddRoundKey, which are described subsequently. The final round contains only 3 transformations, and at that place is a initial single transformation (AddRoundKey) before the low round, which can embody considered Bout 0. Each transformation takes one or much 4 * 4 matrices as input signal and produces a 4 * 4 matrix as output. Figure of speech 5.1 shows that the output of each round is a 4 * 4 matrix, with the output of the terminal round out beingness the ciphertext. Also, the key expansion function generates N + 1 roundish keys, each of which is a distinct 4 * 4 ground substance. Each labialize key serve as one of the inputs to the AddRoundKey transformation in from each one troll. Detailed Bodily structure Calculate 5.3 shows the AES cipher in Sir Thomas More detail, indicating the sequence of transfor- mations in each round and showing the corresponding decryption function. As was done in Chapter 3, we show encoding proceeding down the page and decryption legal proceeding up the Sri Frederick Handley Page. Before delving into inside information, we can make several comments about the total AES social structure. 1. One notable have of this structure is that it is non a Feistel structure. Recall that, in the classic Feistel structure, half of the information block is accustomed modify the other half of the data block and then the halves are swapped. AES instead processes the entire information block as a single matrix during each round victimisation substitutions and permutation. 2. The key that is provided as stimulation is swollen into an array of 40-four 32-bit words, w [i]. Four distinct run-in (128 bits) service A a orotund key for each round; these are indicated in Figure 5.3. 3. Iv different stages are used, ane of permutation and three of commutation: • Unreal bytes: Uses an S-box to do a byte-away-byte substitution of the block • ShiftRows: A simple permutation • MixColumns: A substitution that makes use of arithmetic over GF(28) • AddRoundKey: A simple bitwise XOR of the current block with a portion of the expanded key 4. The anatomical structure is quite naif. For some encryption and decipherment, the cipher begins with an AddRoundKey stage, followed away nine rounds that apiece includes all quaternion stages, followed by a tenth circle of three stages. Figure 5.4 depicts the structure of a full encryption round. 5. Only the AddRoundKey poin makes function of the key. For this reason, the cipher begins and ends with an AddRoundKey stage. Any separate stage, practical at the first or end, is reversible without knowledge of the key out and so would add no surety. 6. The AddRoundKey arrange is, in effect, a form of Vernam cipher and by itself would not be unnerving. The other terzetto stages together provide confusion, dissemination, and nonlinearity, but by themselves would provide zero security because they do not use the winder.We can sentiment the cipher as cyclical operations of XOR encryption (AddRoundKey) of a blank out, followed away scrambling of the block (the other three stages), followed past XOR encryption, and so on. This scheme is some underspent and extremely secure. 7. Each stage is easy reversible. For the Substitute Byte, ShiftRows, and MixColumns stages, an inverse social function is utilized in the decryption algorithmic program. For the AddRoundKey stage, the inverse is achieved by XORing the synoptic round key to the block, using the effect that A Ⓧ B Ⓧ B = A. 8. As with most block ciphers, the decryption algorithm makes consumption of the dilated key in annul order. However, the decryption algorithm is not monovular to the encryption algorithm. This is a consequence of the fussy structure of AES. 9. Formerly it is established that all quatern stages are revocable, it is uncomplicated to swear that decryption does recover the plaintext. Pattern 5.3 lays out encryption and decipherment going in opposite vertical directions. At each horizontal bespeak (e.g., the dotted line in the figure), State is the same for some encryption and decryption. 10. The final disklike of both encoding and decryption consists of merely 3 stages. Again, this is a moment of the particular structure of AES and is required to make the cipher reversible. 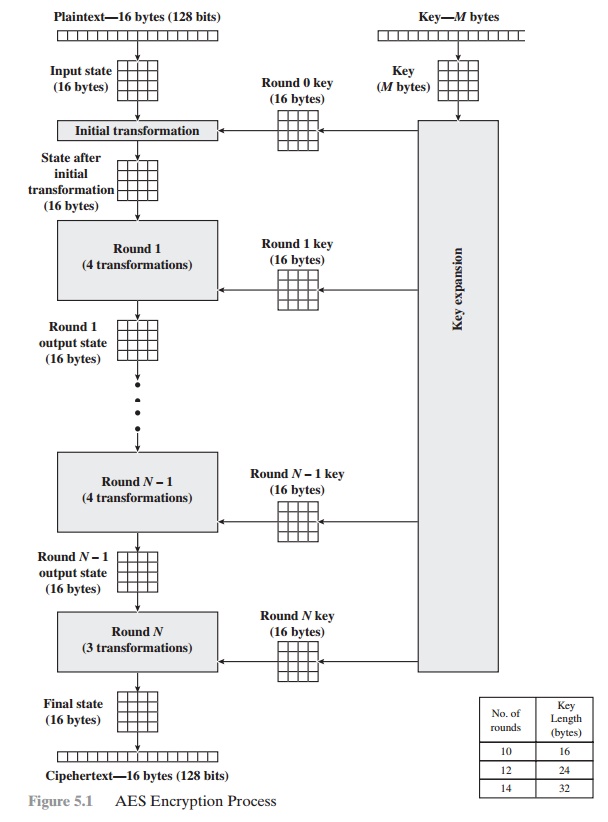
Study Material, Lecture Notes, Assignment, Reference, Wiki description explanation, abbreviated item
Cryptography and Network Security Principles and Practice - One and only Bilateral Ciphers - Advanced Encryption Standard : AES(Advanced Encryption Standard) Structure |
The Aes Cipher Consists of N Rounds, Where the Number of Rounds Depends on the
Source: https://brainkart.com/article/AES(Advanced-Encryption-Standard)-Structure_8408/
0 Response to "The Aes Cipher Consists of N Rounds, Where the Number of Rounds Depends on the"
Postar um comentário